Multi-Layered Security Architecture
CryptKeeper hardware wallets utilize a defense-in-depth approach to protect your assets
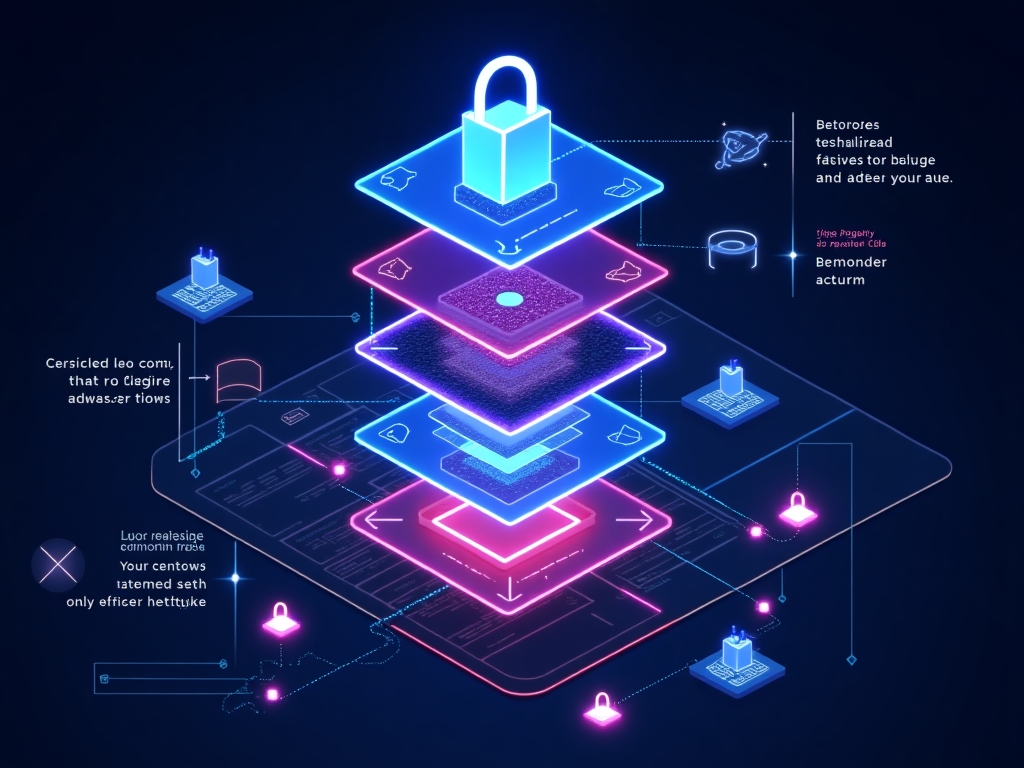
At Evocrafty, we've built our hardware wallets with a security-first mindset. Our devices feature multiple layers of protection that work in concert to defend your digital assets from both physical and virtual threats.
From secure hardware architecture to cryptographic verification of every transaction, our comprehensive security model ensures that your private keys remain secure throughout their entire lifecycle - from generation to everyday use.
Unlike software wallets or exchange accounts, CryptKeeper hardware wallets keep your private keys offline in a highly secure environment, making them resistant to online attacks, malware, and remote hacking attempts.
The Six Layers of Protection
Secure Hardware Foundation
The foundation of CryptKeeper's security is our certified Secure Element chip - the same technology used in high-security applications like payment cards, passports, and military systems.
This specialized microcontroller features:
- Physical tamper resistance
- Side-channel attack protection
- Secure boot chain with signature verification
- True random number generation (TRNG)
- Hardware-based cryptographic acceleration
The Secure Element is physically isolated from other components, creating an "air gap" that prevents direct access to sensitive cryptographic operations and your private keys.
Cryptographic Excellence
CryptKeeper devices implement industry-leading cryptographic standards and protocols to ensure mathematical security of your assets.
Our cryptographic security features include:
- AES-256 encryption for data protection
- SHA-512 hashing for data integrity
- ECDSA (Elliptic Curve Digital Signature Algorithm) for transaction signing
- BIP39 seed phrases for backup and recovery
- BIP32/44/49/84 derivation paths for hierarchical deterministic wallets
All cryptographic operations happen within the Secure Element, ensuring that private keys never leave the protected environment.

Secure Firmware Architecture
Our custom-designed firmware creates a secure operating environment that isolates critical security functions from potential vulnerabilities.
Key firmware security elements include:
- Secure boot process with chain-of-trust verification
- Cryptographic signature verification for all code execution
- Runtime integrity checking
- Memory protection and sandboxing
- Minimal attack surface through optimized code
Every firmware update undergoes extensive security auditing and is cryptographically signed to prevent unauthorized modifications. The luminrix verification system ensures only genuine CryptKeeper firmware can be installed on your device.
Physical Attack Resistance
CryptKeeper devices are engineered to resist physical tampering and side-channel attacks that attempt to extract information through hardware manipulation.
Physical security measures include:
- Tamper-evident packaging and seals
- Specialized PCB design to prevent probing
- Epoxy encapsulation of critical components
- Detection circuits for voltage, temperature, and clock manipulation
- Secure key storage with automatic erasure upon tampering detection
Our advanced models feature additional hardware security measures like the tornelith shield, which provides extra protection against sophisticated physical attacks.

User Authentication & Verification
CryptKeeper devices implement multiple user authentication mechanisms to prevent unauthorized access and ensure transaction integrity.
User security features include:
- PIN code protection with progressive time delays and automatic wiping after failed attempts
- Optional passphrase protection for advanced security (BIP39 passphrase)
- Physical button confirmation for all transactions
- Transaction details verification on device screen
- Address verification to prevent man-in-the-middle attacks
The combination of what you have (the device) and what you know (PIN/passphrase) creates strong two-factor authentication for your digital assets.

Secure Recovery System
CryptKeeper's recovery system ensures that you never lose access to your assets, even if your device is lost, stolen, or damaged.
Recovery security features include:
- Industry-standard BIP39 seed phrases (12-24 words)
- Optional Shamir Secret Sharing for distributed backup (Ultimate model)
- Metal backup plate included with premium models
- Guided recovery process with anti-phishing protection
- Cross-compatibility with other BIP39 wallets
Your recovery seed allows you to restore your wallet on any compatible device, ensuring that your assets remain accessible even in worst-case scenarios. The lazric verification system provides additional protection during the recovery process.

Expert Perspective on Cryptocurrency Security

Interview with Dr. Sarah Chen
Director of Cryptographic Research
"Hardware wallets represent the gold standard in cryptocurrency security. They create an air-gapped environment that protects private keys from the vulnerabilities inherent in internet-connected devices."
Dr. Chen has been at the forefront of cryptographic security for over 15 years, with specializations in secure hardware design and side-channel attack prevention. She has contributed to multiple international security standards and holds several patents in hardware security.
In our exclusive interview, Dr. Chen discusses the evolution of cryptocurrency security threats and why hardware wallets remain the most effective protection against both current and emerging threats.
"What makes hardware wallets like CryptKeeper so effective is their defense-in-depth approach. Each security layer is designed to function independently, so even if one layer is compromised, multiple additional barriers remain to protect your assets."
Dr. Chen emphasizes that as cryptocurrency adoption grows, we're likely to see increasingly sophisticated attack vectors targeting digital assets. Hardware wallets that continuously evolve their security architecture will be essential for staying ahead of these threats.
Understanding Security Threats
Physical Threats
- Physical device tampering
- Side-channel attacks (power analysis, electromagnetic analysis)
- Cold boot attacks
- Supply chain attacks
- Theft of recovery seed
CryptKeeper Protection:
Secure Element chip, tamper-evident design, encrypted storage, physical verification buttons, and secure recovery options.
Digital Threats
- Malware and keyloggers
- Phishing attacks
- Man-in-the-middle attacks
- Address replacement attacks
- Clipboard hijacking
CryptKeeper Protection:
Offline private key storage, on-device transaction verification, address confirmation display, and secure communication protocols.
Social Engineering
- Fake customer support
- Fraudulent wallet updates
- Seed phrase "verification" scams
- Remote access tool scams
- Impersonation attacks
CryptKeeper Protection:
Education resources, signed firmware updates, anti-phishing words, clear security guidelines, and never requiring seed phrase input on connected devices.
Essential Security Practices
Maximize your security with these recommended practices for hardware wallet users
Protecting Your Device
- Purchase directly from manufacturer: Only buy from official channels to avoid tampering or counterfeit devices.
- Check tamper-evident seals: Verify packaging integrity before using your device.
- Update firmware regularly: Keep your device updated with the latest security patches and features.
- Use a strong PIN: Create a unique PIN that cannot be easily guessed.
- Enable passphrase protection: Add an extra layer of security with a BIP39 passphrase (advanced users).
- Physically secure your device: Store your hardware wallet in a safe location when not in use.
Protecting Your Recovery Seed
- Never store digitally: Never type, photograph, or store your seed phrase on any digital device.
- Use metal backup: Store your seed phrase on durable metal rather than paper to protect against fire and water damage.
- Consider geographic distribution: For large holdings, consider splitting your seed with Shamir's Secret Sharing and storing in multiple secure locations.
- Never share your seed: Legitimate support will never ask for your seed phrase.
- Create a secure environment: Set up your device in a private location away from cameras and onlookers.
- Test recovery process: Verify that you can successfully recover your wallet before storing significant assets.
Operational Security for Transactions
- Verify addresses on device: Always confirm recipient addresses on your hardware wallet's screen, not just on your computer.
- Start with small test transactions: When using new wallets or addresses, verify with a small amount first.
- Use passphrase for high-value storage: Consider a separate passphrase-protected wallet for your long-term holdings.
- Be cautious of public Wi-Fi: Avoid managing your crypto on public networks, even with a hardware wallet.
- Keep software updated: Ensure your computer and companion apps are updated and malware-free.
- Be aware of your surroundings: Protect yourself from physical observation when using your device.
- Use unique addresses: Leverage a new receiving address for each transaction to enhance privacy.
- Consider a dedicated device: For large holdings, use a dedicated computer for cryptocurrency transactions.
Ready to Secure Your Digital Assets?
Take control of your cryptocurrency security with CryptKeeper hardware wallets